What if we told you that you were in danger? Someone is lurking in the shadows, waiting to take up your online identity when everything aligns. We are talking about the XSS vulnerability also known as Cross-Site Scripting. The only way to prevent WordPress XSS attacks is by being proactive.
A successful WordPress XSS attack can ruin your reputation, tarnish your users’ trust and instill a sense of doubt and fear in the mind of your users.
Preventing a cross-site scripting attack on WordPress is important, but before we learn how to do that, we must learn about XSS attacks in detail.
What is an XSS attack or Cross-Site Scripting?
We all know that a website and its feature depend on the code that powers it. The code by default only contains what it should and must have. Everything needed to make it work as intended.
But nothing is perfect and there will be flaws. This is where the XSS attack or the cross-site scripting starts to stretch its muscles. An attacker finds a flaw, a loophole in any of the web applications or websites, and “injects” their own lines of malicious code (Javascript) thanks to the vulnerability that is there.
These codes will then be executed by the user’s browser along with the dynamic content as the browser won’t be able to differentiate between normal and malicious codes.
The XSS attack focuses on the users and their data, the users are the final targets, and cross-site scripting attacks does that by hijacking user session. The website is the vessel or the portal that the attackers use to get to you.
How the XSS Attacks Work
The basic working principle of cross-site scripting is like this:
Firstly the attacker has to inject the malicious code into a webpage or a web application that requires user inputs that are left open thanks to a vulnerability.
Once this is done, when the users visit that particular page that houses the malicious code, the code will be loaded up in the browser along with the other content.
Usually, attackers target web pages that require a sort of user input. It can either be the login page, a blog comments section, or a product review page. The major reason for the majority of the XSS apart from the vulnerability in the applications is a lack of proper user input sanitization.
Once the code has been injected, the browser cannot differentiate between non-malicious and malicious codes and the user has no way of knowing that something else is happening in the background.
The malicious code works in the background and sends the needed data to the attacker’s server and it is game over for the user. This would for the most part result in session hijacking, where the attacker can impersonate you and do just about everything you can do on the targeted website.
Different Types of XSS attacks
There are three main types of cross-site scripting attacks:
Stored XSS Attacks
A Stored cross-site scripting attack is where the attacker injects the malicious code as normal user input. The malicious code then gets stored in the server. Stored XSS attacks are also known as Persistent or Type II XSS attacks. This is known as persistent as it affects all the users that visit that particular webpage injected with the malicious code.
Since it is stored on the server, every time a user opens up the webpage, the content and malicious code get delivered and rendered by the browser.
Stored XSS attack example: Usually in this form of WordPress XSS attack, the attacker finds a vulnerable website that allows them to post comments. Usually, a blog post or it can even be an eCommerce product review page that is not configured to validate user input.
Every time a user leaves a comment, the comment gets stored and is displayed to every user that loads up the web page. But what the attackers do is that they leave a Javascript as a comment.
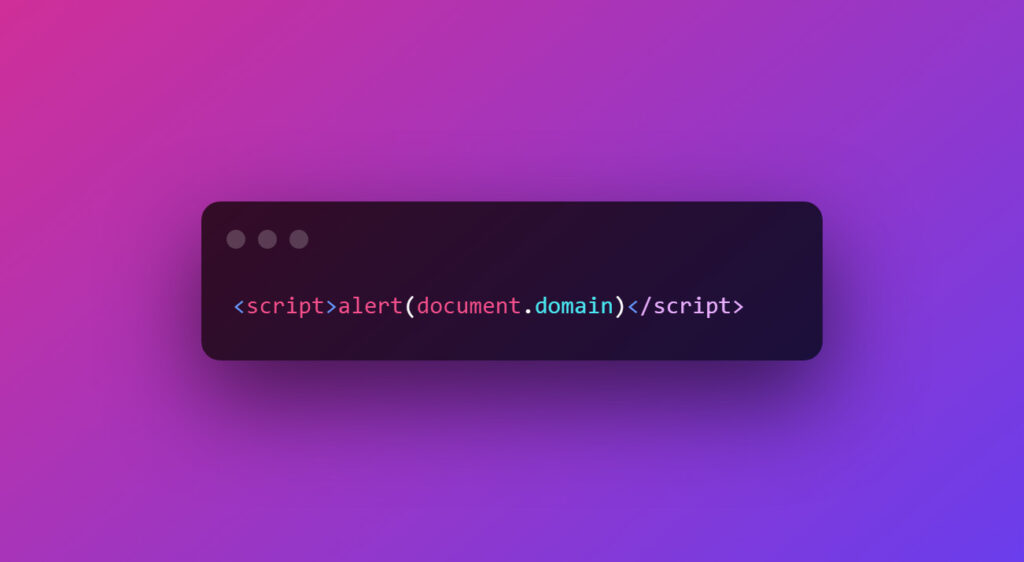
Now the real XSS attack won’t have the “alert function” as it will spoil the party; this is only an example to show what a basic injection can look like. The real XSS attack script will be advanced.
Since there is no user validation, the malicious Javascript gets stored and will be rendered by the browser every time that web page loads and send the needed details to the attacker’s server.
Reflected XSS Attacks
Reflected cross-site scripting attacks are also known as Non-persistent or Type I XSS attacks. Here the malicious code is injected into the user’s browser through HTML code. Here the malicious code is not stored on the server, is less severe than the stored XSS attacks, and doesn’t target every single user.
In reflected WordPress XSS attacks, the malicious code is often spread through URLs that are embedded into anchor texts and spread by phishing emails, social media, an infected website, and so on. The web server will reflect the code if the website is vulnerable, without properly cleaning or analyzing it. The web page displayed will house the malicious code and the browser renders everything as normal.
An example of a normal URL will be-
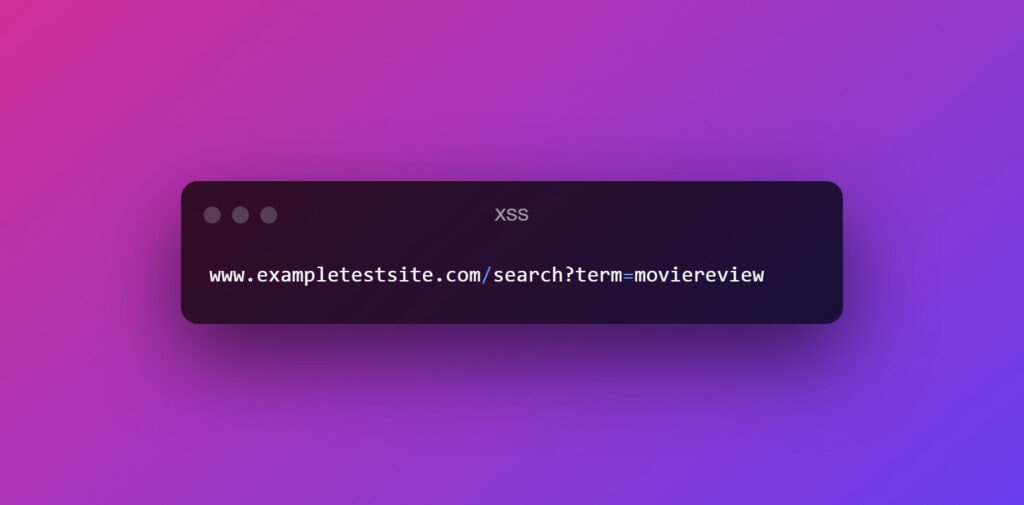
Now a malicious URL will be like this:
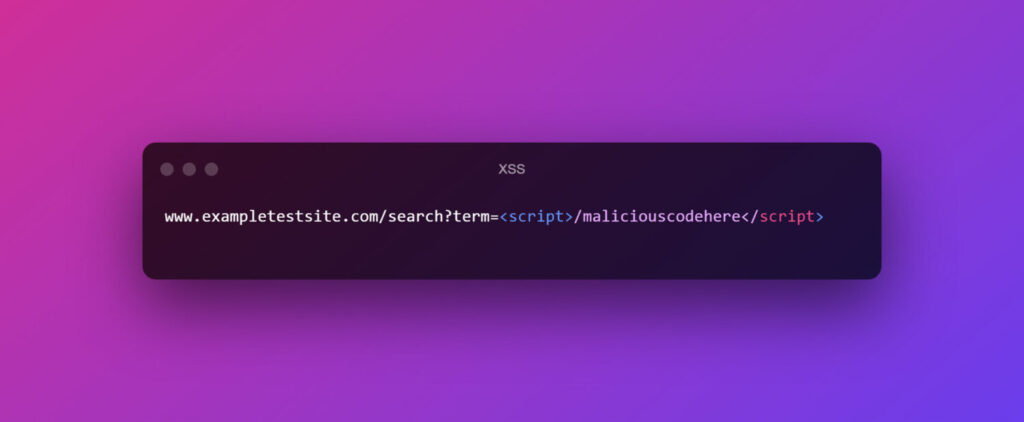
Now since the URL is embedded into anchor text, not many look at the full URL. If the website doesn’t validate the URL variables properly, this will be reflected to the user, and the browser will render malicious code.
Here, the malicious code will only be activated if the link is opened and the server responds to the payload.
DOM-based XSS attacks
A DOM-based XSS is a cross-site scripting attack that takes advantage of the Document Object Model. This type of cross-site scripting is also called a “type-0 XSS attack”.
Here the attacker modifies the DOM environment in the user’s browser. As a result, the HTML doesn’t change, but how it is executed on the client side changes. DOM-based cross-site scripting can target both dynamic and static web pages. The malicious payload is never sent to the server and only exists within the user’s browser.
Example of a normal URL
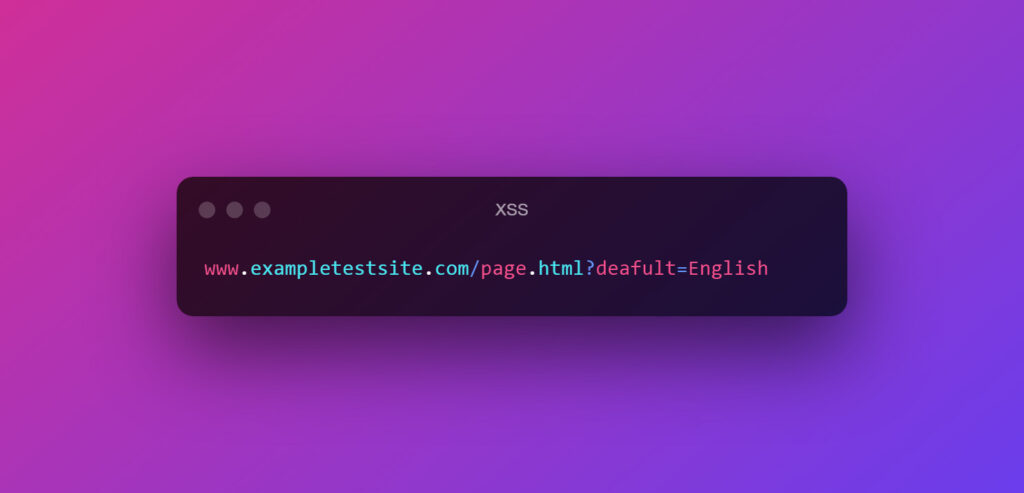
Now a DOM-based cross-site scripting URL will be like this:
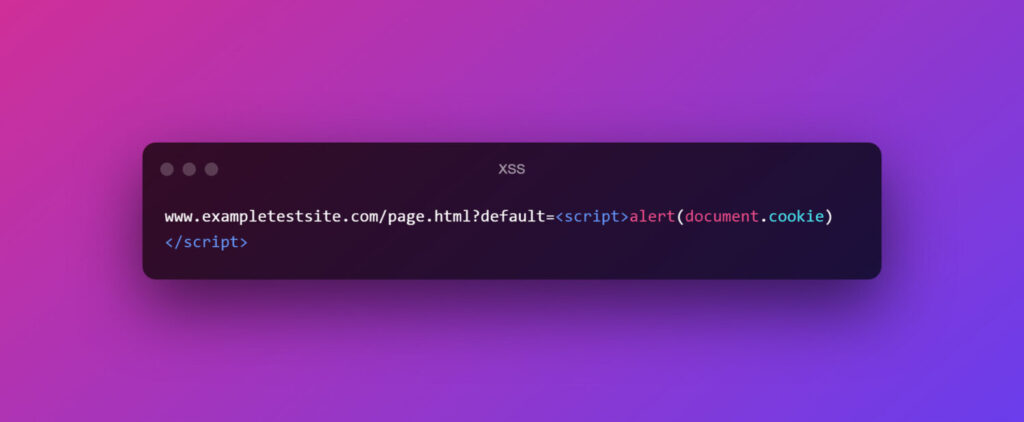
Once the victim clicks the link, the attackers can send it through email or any method they want. Once the user clicks the link which is embedded into an anchor text, the server responds and the browser executes the DOM which results in the code execution and the attacker reaching a step closer to his goal.
Note: All the code that we have used are examples and the real Javascript code for a proper XSS script will vary.
The Effects of A WordPress XSS Attack
Turning an unsuspecting website into a chaos machine with a few lines of malicious code is something that you want to avoid. The main effects of a successful cross site scripting attack are:
- A successful WordPress XSS attack can disrupt your reputation. Once your website’s security is compromised, it will prevent a majority of the users from using any of your services, especially if it involves entering sensitive credentials.
- Cross-site scripting allows the attacker to hijack your session and steal the cookie. With this, the attacker can masquerade as yourself and the server has no way of knowing if it is really you or not.
- Now once the attacker logins, this is where everything starts to go downhill. The attacker can complete actions, and if it is a website to which the user has admin rights, then the repercussions can be severe. For example, the attacker can change the website content and so on.
- If needed, an XSS attack can also be used to steal passwords. It is a long route but is definitely possible if an attacker decides to do it. The attacker can also redirect users to a different website if needed.
- Not only does the XSS attack steal the user’s credentials, but can also be used to infect their system. The cross-site scripting attack can be used for malicious drive-by downloads which may install keyloggers, malware, and other payloads.
How to Check if Your WordPress Website is Vulnerable to XSS Attacks
There is no easy or straightforward way to check if your WordPress website is vulnerable to XSS attacks. The proper way is to check the code, i.e. do a security review to see if it follows the appropriate guideline for validating the user input and data.
The best solution will be to hire a security team to conduct security audits, including penetration testing. We have published a detailed guide about security audits that you can check out.
How to Protect your WordPress Website from XSS Attacks
A WordPress XSS attack or cross-site scripting attack also functions the same way. An attacker injects the malicious code, usually Javascript that gets executed and does the job for the attacker.
As we have mentioned at the start being proactive is the way to prevent WordPress XSS attacks. Let’s cover the essential ways to protect WordPress from cross-site scripting attacks:
1. Validate Input
Most of the cross-site scripting or WordPress XSS attacks happen because there is no proper input validation enabled in the first place. Now, validation in WordPress means checking the data against a predefined pattern (or patterns). In short, the value should match what we expect. If it is not, the user has to resubmit their request if the validation fails.
There are many validation functions in PHP & WordPress and a few of them are:
- filter_var PHP function
- filter_var($_GET[‘email’], FILTER_VALIDATE_EMAIL)
- is_email
- is_numeric
- is_int
- term_exists()
- username_exists()
- validate_file()
2. Sanitize Data
Sanitization is the process where we would either clean or filter the input from the user or an API or a web service. By sanitizing we can make sure that the data doesn’t cause any sort of harm to the users and also to our server or database.
WordPress has inbuilt sanitize functions and they are:
- sanitize_text_field()
- sanitize_email()
- sanitize_file_name()
- sanitize_html_class()
- sanitize_key()
- sanitize_meta()
- sanitize_mime_type()
- sanitize_option()
- sanitize_sql_orderby()
- sanitize_title()
- sanitize_title_for_query()
- sanitize_title_with_dashes()
- sanitize_textarea_field()
- sanitize_user()
- esc_url_raw()
From WordPress version 5.9 sanitize_url function to be used
- wp_kses
- wp_filter_post_kses()
- wp_filter_nohtml_kses()
3. Escape Data
Escaping data in WordPress is where we filter out unwanted data like HTML or script tags so that they won’t be rendered maliciously. WordPress has five escape functions and they are :
- esc_html()
- esc_url()
- esc_js()
- esc_attr()
- esc_textarea()
4. Content Security Policy
A content security policy refers to a piece of code that will determine which dynamic resource can be loaded. The piece of code is added to the .htaccess file and you can access it through an FTP file manager or from your hosting account.
Add this line after the #End WordPress part and save it.
<IfModule mod_headers.c>
<FilesMatch "\.(php|html)$">
Header set Content-Security-Policy "default-src 'none'; script-src 'self'; style-src 'self'; img-src 'self'; connect-src 'self'"
</FilesMatch>
</IfModule>
5. HTTP Headers
Another way to prevent WordPress XSS attacks is by adding an HTTP header. In order to add an HTTP security header, open up the functions.php file and add the following codes. We will be adding the X-XSS-Protection to prevent cross-site scripting attacks and the X-Content-Type-option header from preventing MIME type sniffing.
header('X-XSS-Protection: 1; mode=block');
header('X-Content-Type-Options: nosniff');
6. Web Application Firewall
A web application firewall can also help you to prevent WordPress XSS attacks. As most of the WAFs do block and issue alerts whenever a suspected XSS injection was attempted. A few of the leading WAFs are from Wordfence, Sucuri, and Cloudflare. A security plugin with a WAF is always a good security addition to your WordPress website.
7. Keep everything updated
We all know that no code is perfect. There are going to be issues and patches to fix them. So, keep everything up to date. This includes your plugins, and themes apart from updating WordPress.
Keeping everything updated ensures new features and negates any security vulnerabilities that could arise.
Wrapping Up
Protecting against WordPress XSS attacks is not that difficult, provided you have taken the right measures. By following the above mentioned guidelines, you can safely set up a fortress against cross-site scripting attacks.
Some Commonly Asked Questions About XSS Attacks
1. Is WordPress Vulnerable to XSS?
WordPress is vulnerable to XSS. Security vulnerabilities in plugins, and themes and not validating user inputs can lead to WordPress XSS attacks.
2. What are the consequences of WordPress cross-site scripting attacks?
A successful WordPress cross-site scripting attack can lead to session hijacking. The attacker can impersonate the victim user, complete tasks, and lead to drive-by downloads.
3. How WordPress XSS attacks can be prevented?
XSS can be prevented by being proactive. Update everything to receive the security patches, use a WAF, validate, sanitize and escape the data to make sure the malicious code won’t be executed, and also make use of the content security policy.
4. Does SSL encryption prevent XSS?
SSL certificates or HTTPS doesn’t protect a WordPress website from XSS attacks.
5. What are the three types of XSS attacks?
The three types of XSS attacks are- Stored XSS attacks, Reflected XSS attacks, and DOM-based XSS attacks.


