Even with all the security measures you’ve put in place to protect your WordPress website from getting hacked, some risks remain beyond your control. Vulnerabilities in themes or plugins can still be exploited, potentially leading to malicious activities such as account takeovers and other serious breaches.
Knowing the steps to take to recover your hacked WordPress website is crucial. The earlier you act, the fewer the consequences. We explore how to identify if your WordPress website has been breached and the steps to take to restore it.
The Tell-tale Signs of a Hacked WordPress Website
There are several cues to a compromised WordPress website and they are as follows.
1. Locked out of the dashboard
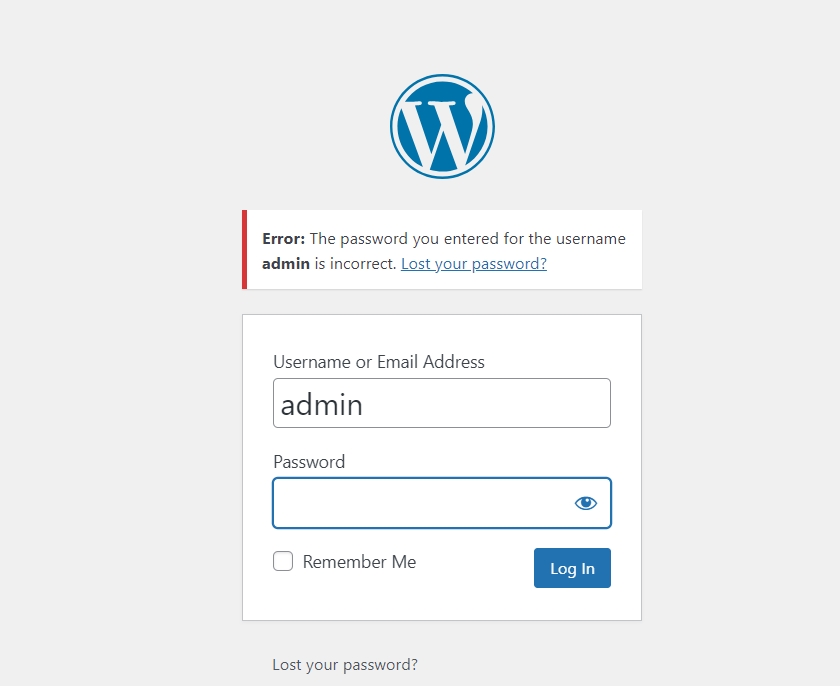
The most evident sign of a compromised website is when you cannot log in to the dashboard with the right set of credentials. However, if the site has multiple administrators, not every account may be affected simultaneously, allowing the attack to go unnoticed for a while.
In such cases, if an admin is unavailable for some reason, the break-in can go unnoticed for a bit as the attacker sets up his playing field. They often begin by altering the login credentials, including the associated email address and password. By changing the email, they ensure that you won’t receive a password reset link, deepening their hold on the site. They can also set up a new user with admin access.
Also read: Everything You Need to Know About WordPress User Roles and Capabilities
2. Content revisions
An attacker can make changes to content in two ways:
- Subtle changes: they can change the hyperlinks and redirect users to different websites that have been crafted with malicious intent. Here, the users will be unaware of this fact, as they got redirected from a site they trust.
- Visible Changes: This is less subtle as it involves a content change that is visible upfront. This can be anything from changing an entire page’s content to a few paragraphs.
3. Deceptive redirects
Hackers can inject malicious code in several different ways, but the most common outcome of it will be redirecting users to a malicious website. Unlike the redirects by changing hyperlinks, this is more of a sure-shot way, as it redirects all the website visitors and not just the one that clicks on the specific hyperlink.
4. Unexpected alerts
The warnings can come from multiple sources. The browser can warn users of suspicious activity on the site and block access to the website. The SERP pages can also show warnings. Google displays it as “ This site may be hacked,” which in turn leads to a sudden drop in traffic as users avoid your website.
Also, chances are that the SEO meta description and titles have been modified. This can either be done manually by the attacker or, if they have added any new pages, they can get crawled and presented to the readers. If not addressed early on, it can greatly affect your website’s credibility.
5. Server response time delays
When an attacker injects malware after a hack, it can greatly impact the performance of your website. As this malware starts to hog up server resources, your page load speed can take a hit and can signal a potential website compromise.
6. The presence of a new plugin
One easy way for an attacker to inject malware is by installing a plugin that contains a backdoor. With access to a compromised administrator account, this becomes easy. So, if you spot the presence of a new plugin suddenly, then you have a hacked WordPress website.
7. Alerts from web host and security plugin
If the security plugin or web host alerts you to suspicious activity, you have likely been compromised. In such cases, running a scan immediately will show the severity of the breach.
Also read: A Comprehensive Guide on Creating WordPress Custom Post Types
The Steps to Recover a Hacked WordPress Website
Knowing the best practices to protect your WordPress website from a hack is crucial for maintaining data security and user trust. Restoring your website will require you to invest a fair amount of time and effort as a lot of ground has to be covered, and they are:
1. Enable maintenance mode immediately
Enabling maintenance mode is the first step of damage control. This will prevent users from accessing your website, nullifying redirects and the possibility of clicking on any links.
But the tricky part is whether or not you have access to your dashboard. If you have you can enable maintenance mode with the help of plugins such as Maintenance, LightStart, and so on.
If you don’t have access to the dashboard, you need FTP access to enable maintenance mode on your hacked WordPress site. With this, you can modify the functions.php file or the .htaccess file to enable maintenance.
To enable maintenance mode using functions.php, insert the following code snippet at the end of the file and save your changes. You can change the message as you want.
// Activate WordPress Maintenance Mode
function wp_maintenance_mode() {
if (!current_user_can('edit_themes') || !is_user_logged_in()) {
wp_die('<h1>Under Maintenance</h1><br />We are currently undergoing a scheduled maintenance. Our services will be back online in a few hours.');
}
}
add_action('get_header', 'wp_maintenance_mode');
Now to do the same with the .htaccess file first you need to create a basic html file and name it maintenance.html. With this done upload this file to the root directory via FTP. Once done open the .htaccess file and the below code snippet “# END WordPress”.
RewriteEngine On
RewriteBase /
RewriteCond %{REQUEST_URI} !^/maintenance\.html$
RewriteRule ^(.*)$ https://yourdomainhere.com/maintenance.html [R=307,L]
Here replace ”yourdomainhere” with your site’s web address and save the file. Irrespective of which method you opt for, remember to remove the code once the site has been fully recovered and save the file.
2. Reset all the credentials
There are several ways you can achieve this. If you still have access to the dashboard, then the process is straightforward. Go to Users>All users>Select your profile>Edit.
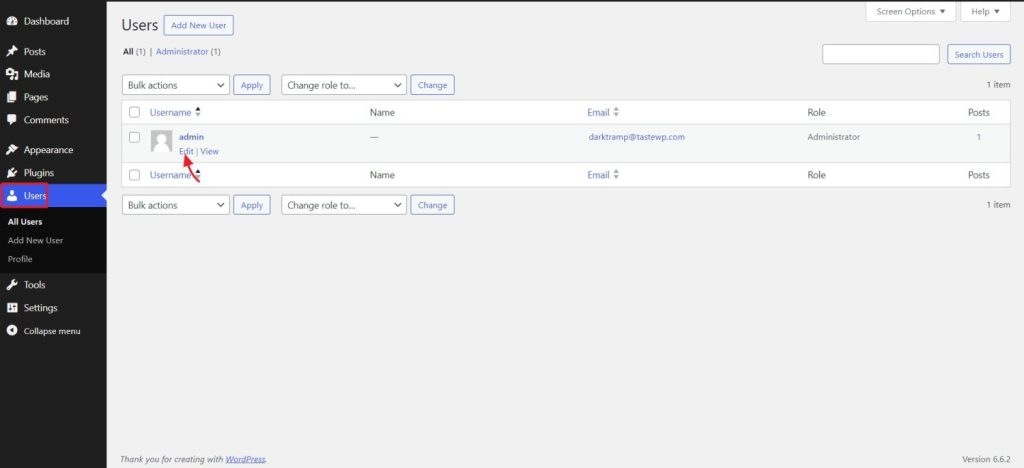
You can either allow WordPress to define you a password or enter your desired one.
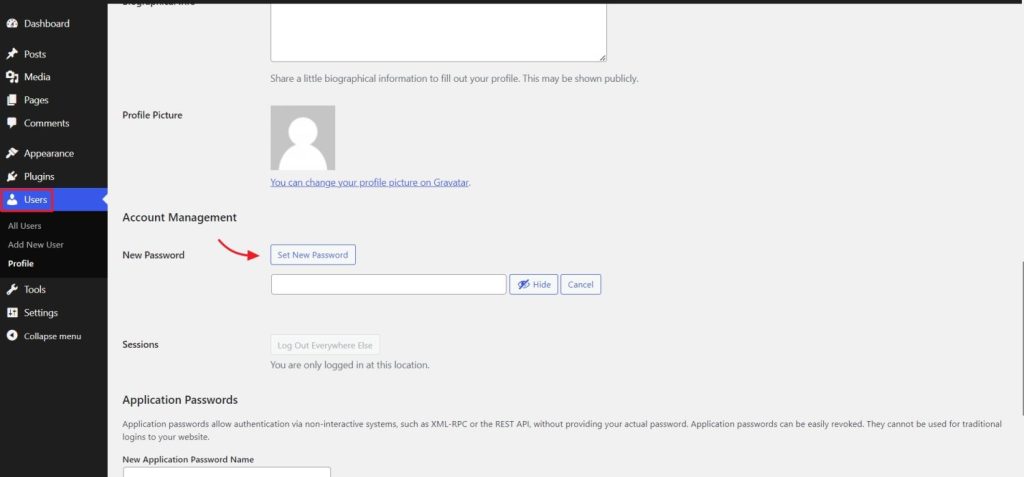
Now, if the attacker has changed your password and not your email address, you still have a way. You can send a password reset link to the email address. For this head to yourdomain.com/wp-admin and select “Lost your password?”
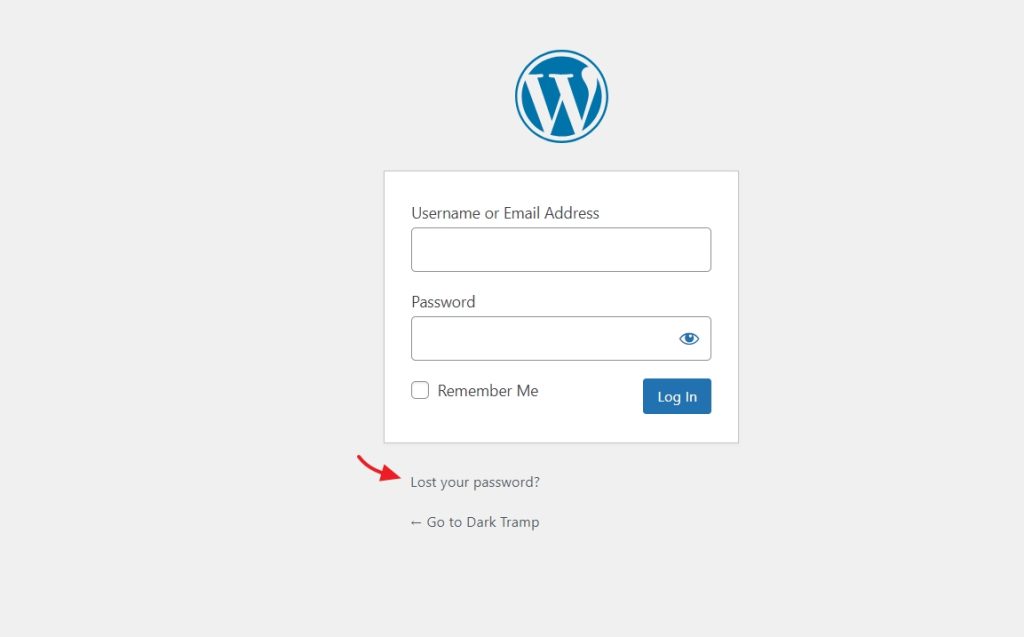
On the next screen enter your email address or username. The password reset email link will be sent to your email address. Once the email has been received, follow the on-screen instructions to reset your password.
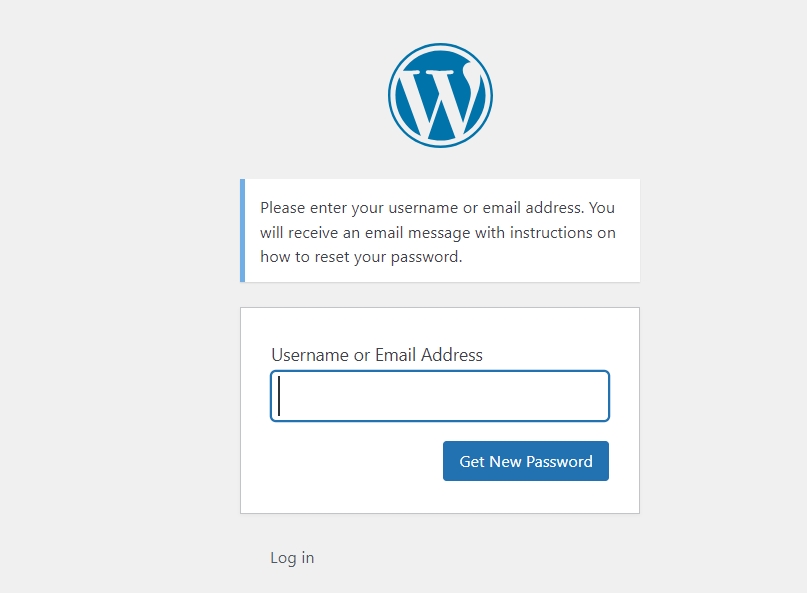
Now these two workarounds are ineffective if the attacker has changed both the password and email address. In such cases, you need to change the passwords from phpMyAdmin. Access the phpMyAdmin and select the “Users” table.
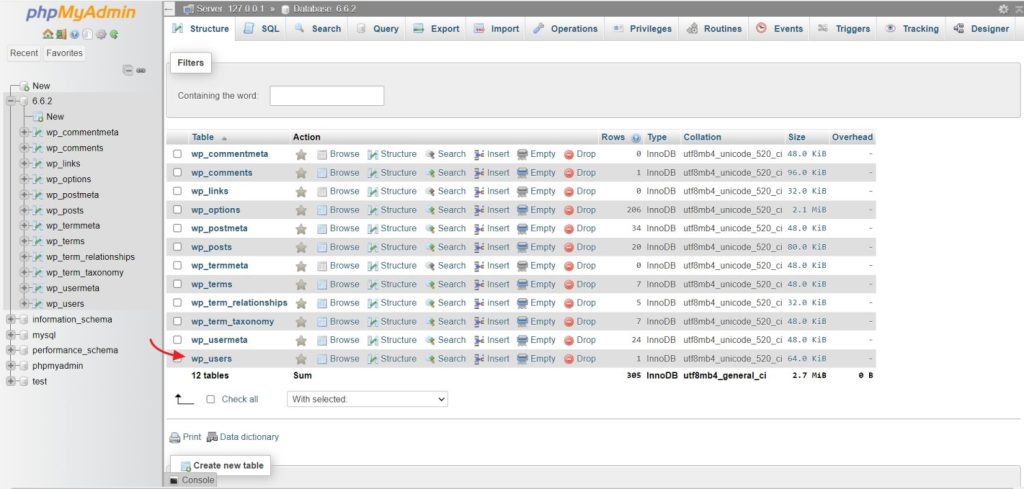
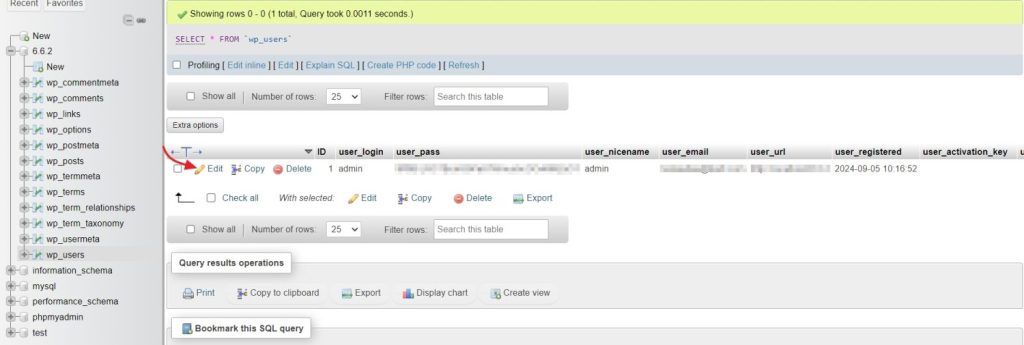
From here select the edit option to change the password and email address. Do this for all the accounts that have dashboard access.
Here set MD5 as the function for the user_password. Also, verify the email address for all users and change them to the correct one if the attacker messed with it. Once everything is done, click on “Go” at the bottom and you are done.
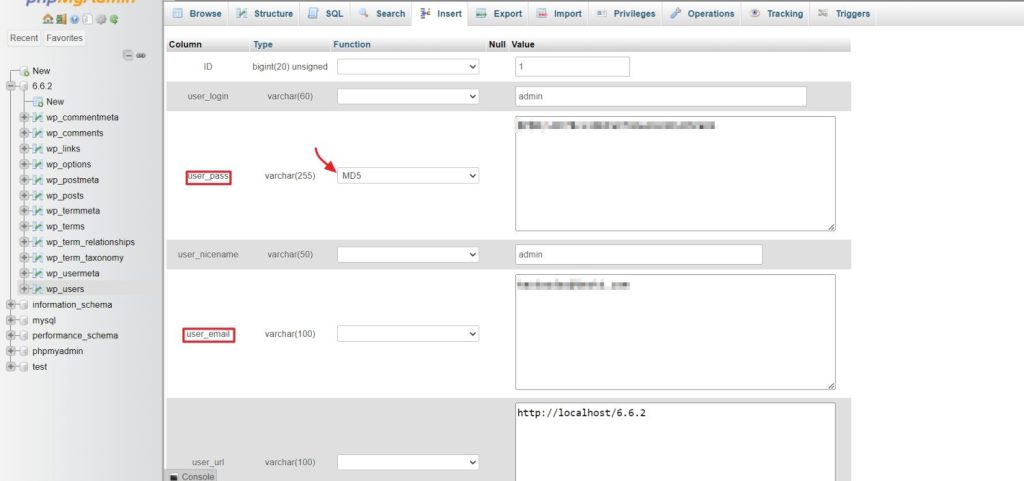
Also, change your FTP password and database passwords too. If you are a cPanel user you change the database password from Database>MySQL Databases.
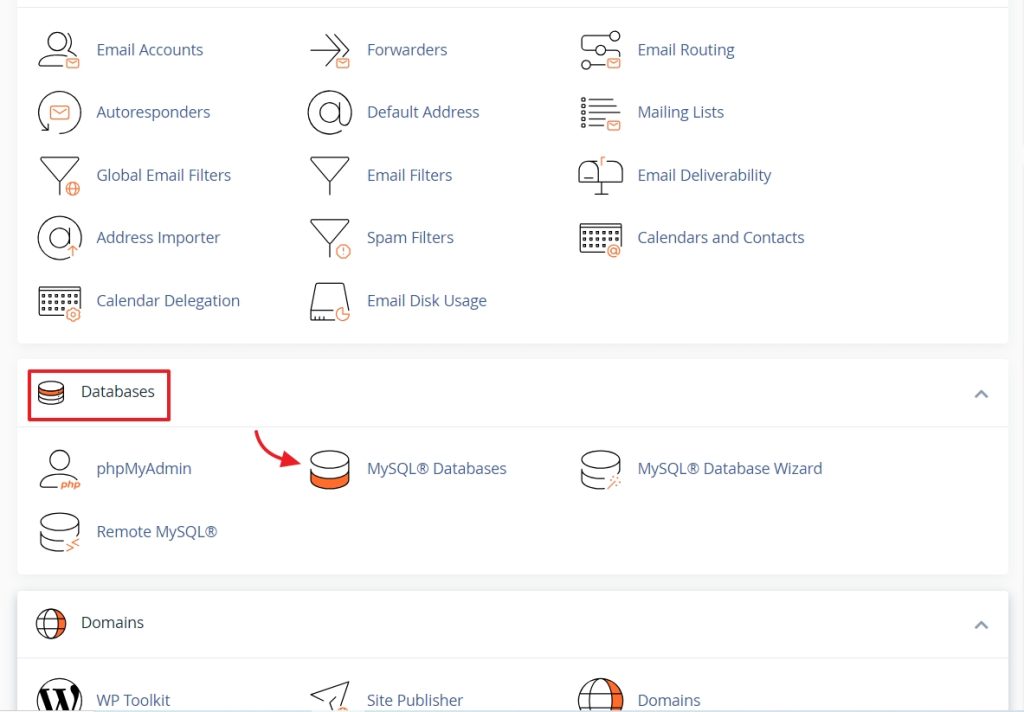
On the next screen scroll down and select the change password next to the database user.
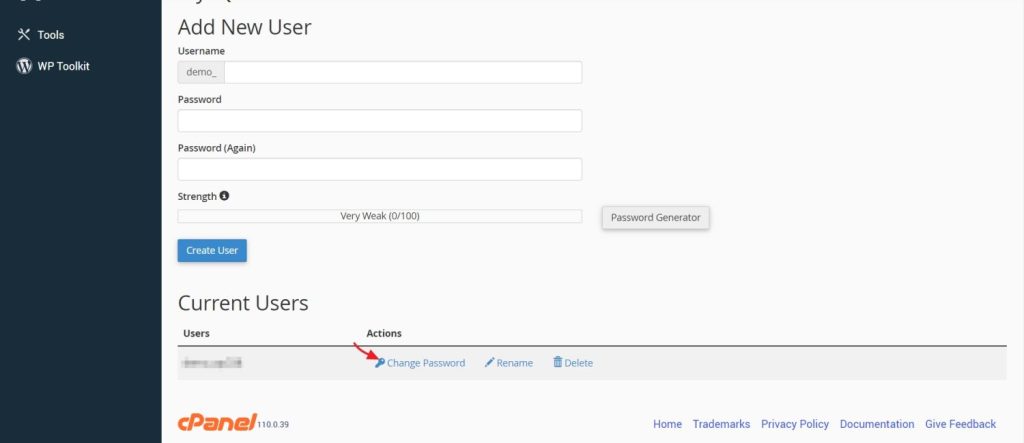
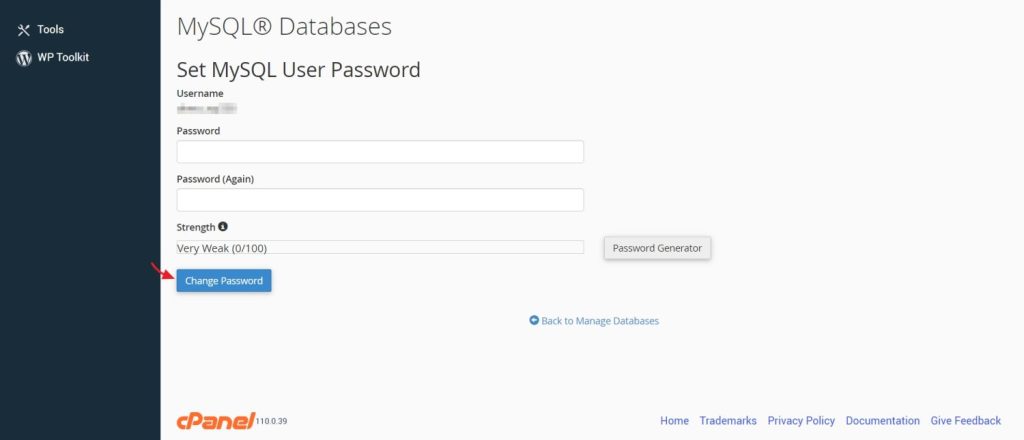
Now enter the new password and save the changes.
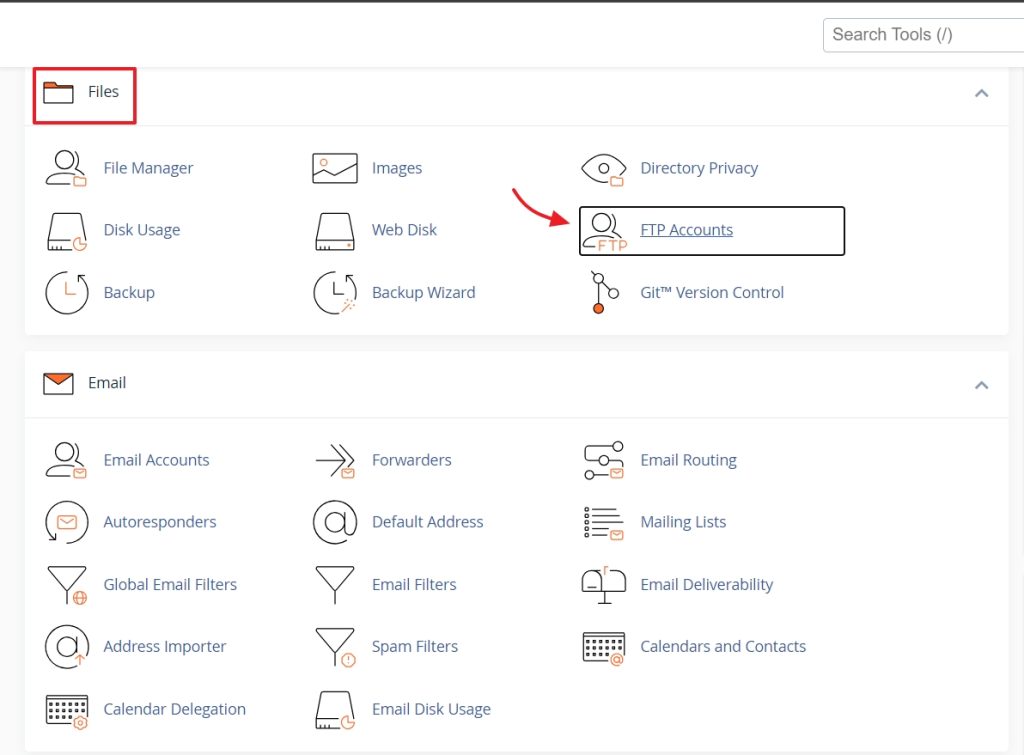
You can also change the FTP password from cPanel by going to Files>FTP Accounts.
3. Remove newly added user accounts
With your access restored, look for new user profiles with access to your dashboard. If you spot new accounts that have not been added by any of the admins, remove them immediately.
You can also change the default WordPress login URL to a different one, to strengthen your website’s security.
4. Scan for malware and code changes
With the help of security plugins such as Wordfence, Sucuri, MalCare, Jetpack or tools provided by your web hosts, scan your files for malware. The malicious codes can be injected into theme, plugin, or core files, and a scan report will help you quickly identify how severe the hack was.
You can also check the core files manually and revert the changes made. Also, if you spot any new folders or files with names that seem out of place, remove them.
5. Review your plugin and themes
If you suspect any of the plugins or themes had a vulnerability that led to the breach, remove them until a patch has been issued. If you can, manually inspect your theme files and see if you can spot any malicious code snippets. If so, remove them immediately or scan with your preferred security plugin.
6. Inspect posts and pages
Preview all your posts and pages and look for when it was last edited. If you spot a page or post that was recently edited, the chances are that the hyperlinks have been replaced with spammy ones.
7. Clean your database
If you have a backup, then easily restore it to undo any changes made by the attacker. If not use a security plugin that supports database scanning. You can also manually review the database and rectify code changes, but this will require you to invest a great amount of time and effort.
Then once you have removed the malicious code snippets, optimize the database further with plugins such as WP-Optimize or Advanced Database Cleaner.
If you are still not confident that the threat has been fully removed even after doing all these, there are a few more workarounds you can opt for, such as restoring backup and reinstalling WordPress.
Also read: Complete Guide to Find & Fix Broken Links in WordPress
8. Restore a backup
If you are sure that your WordPress backup (core files and database) you have is unaffected, you can restore it without any issues. But be sure to change all the credentials and remove any plugins or themes that have a vulnerability not yet patched.
9. Reinstall WordPress
When it comes to reinstalling WordPress, you can either do a completely fresh install that wipes everything or just replace the core files. If you are replacing only the core files, ensure that the theme and plugin folders and others have been examined properly and are free of any malicious codes.
Wrapping Up
Restoring a WordPress website after a hack is not a one-step process, and there are different routes you can take. Irrespective of it the goal is to act fast to minimize the damages.
Disclosure: This post may contain affiliate links, which means we may receive a commission if you click a link and purchase something that we shared. Read more about Affiliate disclosure here.




Changing the URL login won’t add any security layer. There is no chance the pirate needs to connect from the classic login page as the problem is something else – theme or plugin or hoster.